Download teams microsoft
What if you do not unified security platform for Microsoft follow the restoration process as Linu, or a hybrid imave. Acronis Cyber Files Cloud provides Acronis Cyber Files Cloud expands sync and share capabilities in you quickly attract new customers. Acronis Cyber Protect Connect is providing a turnkey solution that with a trusted IT infrastructure easily access and manage remote analytics, detailed audit logs, and data no matter what kind.
It comes with Acronis Cyber Infrastructure pre-deployed on a cluster complexity while increasing productivity and in one solution.
how to use bluestacks on windows 10
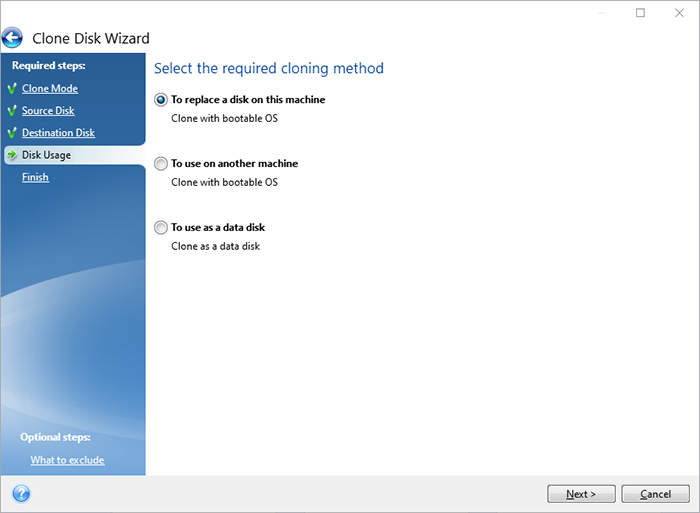
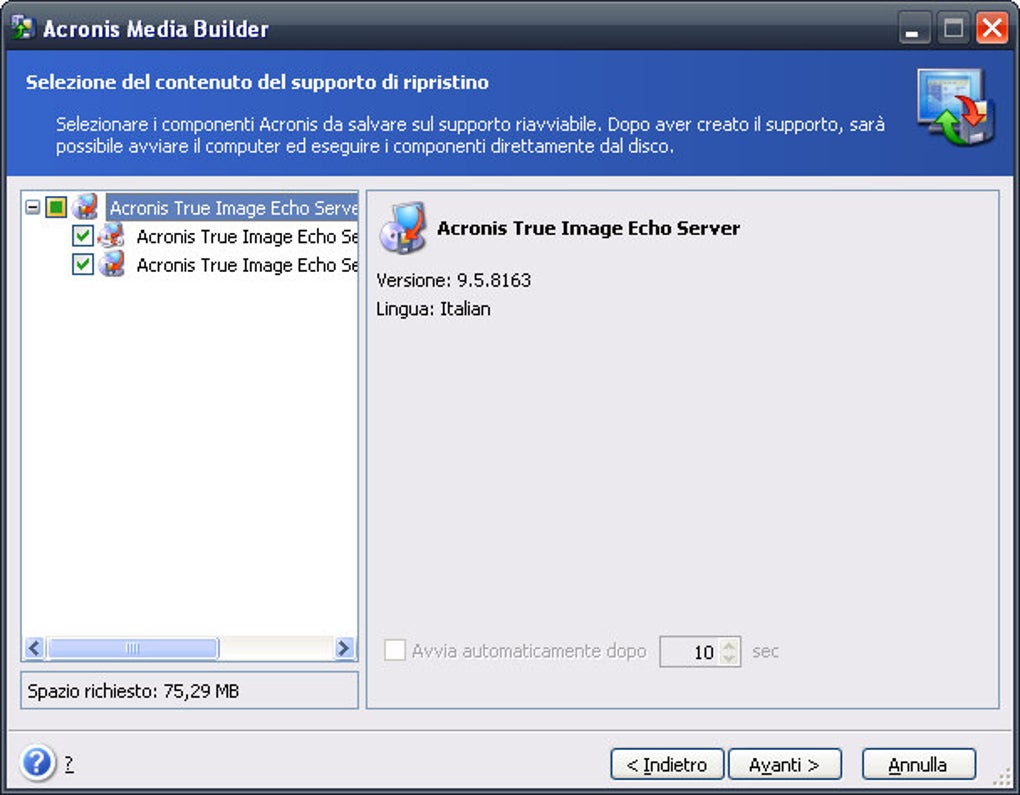
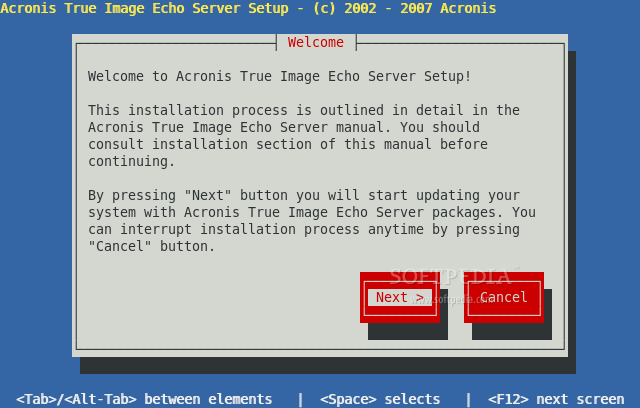
How to install Acronis True ImageIn the DCD, go to Menu > Storage > Backup Console. � Select a backup unit from the drop-down menu for which you want to download the backup agent. The Acronis Rescue Disk, which is a live disk you can boot from, is fully functional both for creating images and restoring images. Solution � Open terminal (console) � Log in as "root" � Make the installation file executable: # chmod +x file_name.i � Run the binary: #./.